Intro:
Normally there are two types of restrictions for shareware. The first one is the demo version with limited or crippled functionality that doesn’t have an expiry date and another type is the fully functional trial version that expires after a certain period of time. The amount of days given to try are normally around 30 days but it could be shorter or longer depending on the author of the software. In the earlier days, you can easily run the expired software by simply backdating the date on your Windows operating system but some software has got smarter to detect this and instantly ends the trial period.
You might think to yourself, how does the shareware knows how many days left in the trial period? Most of the time these commercial and freeware protectors drop some information somewhere deep inside your computer after installation so they know when it was installed and then comparing with the official current time pulled from the Internet. It is possible to find the location that records that information by using file or registry monitoring software including third party uninstaller software such as Revo Uninstaller but it can be tedious and frustrating work.
Here’s a few simpler ways on how you can extend the trial period of software using various different methods.
1.
NirSoft RunAsDate
As the name might suggest, RunAsDate performs a trick on the trial software that has expired by injecting the time and date you specify into its process. This has a similar effect to manually setting your system clock to a different time and date, but in this instance your real clock remains unchanged. RunAsDate can also have multiple instances of its program running at once, and each one can have a separate date, all different to the real one.
As a simple example, if you’re using the popular archiver WinZip and its 30 day trial period has expired, it won’t let you use the program anymore, and you either have to purchase a license or uninstall it. Using RunAsDate, you can set the date back to be within the trial period making WinZip usable again. The image below is WinZip after the 30 day trial has passed, note the “Use Evaluation Version” is now grayed out.
If you now load up RunAsDate, all you have to do is browse for the application to use the program on, in this case “C:\Program Files\WinZip\WINZIP32.EXE”, then choose a date and time from the pop-out calender to before the trial period expired. Now simply press the Run button.

RunAsDate has a few other options such as allow arguments to be applied to the executable, and also a useful option to create a desktop shortcut which will automatically launch the application with the configuration options you’ve supplied in the window. The Immediate Mode check box can be used to inject the date/time earlier in the process, but is known to cause crashes on some programs, especially those using .NET.

If you run WinZip after entering the right date and time numbers and press Run or launch it via a shortcut, you’ll notice it no longer says expired and the Evaluation button is clickable again. Although time and date altering isn’t going to work on all trial software that has an expiry, it is a very quick and easy thing to try out first before turning to more advanced methods.
>>>>Click here to get Run as Date<<<<
2.
Trial-Reset 4.0
This is the final version released in 2010 by “The Boss”, and is able to scan and remove 45 types of commercial and freeware protections including some software that uses custom protectors such as Reflexive, Namo, ABBYY, WinRAR, WinZip and etc. In fact if you know the registry location of where the trial information are recorded for a shareware program, you can create your own text file and save it in the Lists folder.
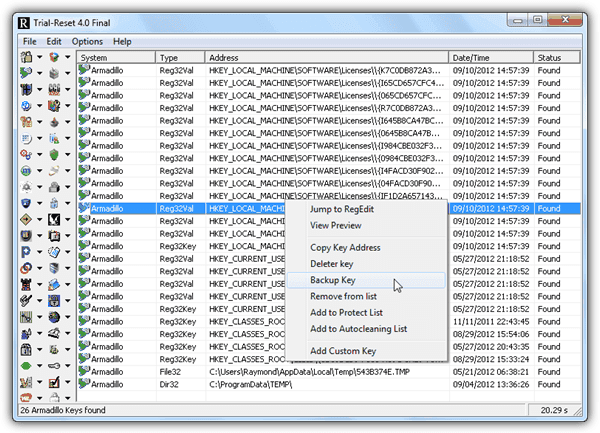
Do note that Trial-Reset does not modify the shareware in anyway. It simply cleans the registry keys generated by the protectors which are normally not removed even after uninstalling the software. This is how a lot of shareware knows you have no trial period left, even if you uninstall and re-install the program again. Trial-Reset is very easy to use. To start scanning, simply click on the All located at the bottom left. The scanning will take a while since some of the methods require scanning the hard drive. The right pane will show all the detected keys that are used by any shareware titles.
You can backup, view or delete the keys, add to protect or auto cleaning list from the right click context menu. If you have a lot of shareware installed, there will be quite a number of results and you will need to do a trial and error to find the key that is associated with the software that you want to reset the trial period.
>>>>Get Trial Reset by clicking here<<<<
3.
Time Stopper
Time Stopper is a program that behaves in a similar way to RunAsDate and fools the expired application into thinking it’s still within the trial period. This tool does differ slightly though because you don’t have the option to directly run the expired program from Time Stopper, but instead it is designed specifically to run from a desktop shortcut with the new time and date injected when you run the program from the shortcut.
Simply run Time Stopper and locate the trial software executable with the Browse button. Choose the new time and date from the pop-out calender, and then give the shortcut icon a name and finish by clicking the create button. Like Nirsoft RunAsDate, this tool will work on some shareware programs and not others but is easy enough to try.
>>>>Click here to Download Time Stopper<<<<
4.
Using a Software Installation Monitor
This method may not seem that obvious at first, but actually can work quite well in many circumstances. The theory is simple in that you use a standard piece of installation monitor software which watches the files and registry entries that a program creates when it installs, and then can completely uninstall the software including everything that doesn’t get removed by the standard uninstaller. This often has the effect of also removing registry entries shareware might leave behind to watch its trial expiry status.
As an example, this can be achieved for the Internet Download Manager shareware program when its 30 day trial expires. We happen to know that the trial status of IDM is stored in the registry key “HKEY_CURRENT_USER\Software\Classes\CLSID\{07999AC3-058B-40BF-984F-69EB1E554CA7}”, but IDM doesn’t remove this key when you uninstall through its own uninstaller and the time/date trick doesn’t work. Therefore once the trial period expires, the information remains on your computer and it will stay expired even if you re-install the program again in future.
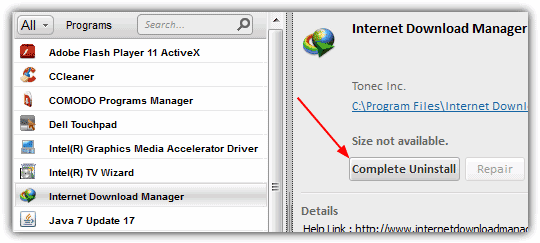
To demonstrate, we installed Comodo Programs Manager which is one of the better installation monitor’s around, and let it automatically monitor the install of IDM. Then once the trial period for IDM has expired, we simply select it for a “Complete Uninstall” in Comodo Programs Manager. After the standard uninstaller has finished, Programs Manager will show the extra files and registry entries that have been left behind. Expand the Registry tree and looking at the keys, we can see the IDM key which controls the trial period status is listed for removal. Continue the removal and if you re-install Internet Download Manager, its trial status will be reset to 30 days.
This method is obviously not foolproof but if you can install the trial software for the first time after installing the installation monitor, and the trial information is kept in the registry or a data file, one of these programs has a chance of picking it up and removing it which will reset the trial period.
5.
Registry Trash Keys Finder
This might be a better solution these days because it is up-to-date. Unlike the Trial-Reset program which was last updated more than 2 years ago, it may not work on shareware that uses a newer version protector. Although Registry Trash Keys Finder is free, there are some limitations where some of the protection keys are not shown. The full version of Registry Trash Keys Finder is only available after donating to the author of this tool and it removes the limit.
As you can see at the screenshot above, there are 3 registry keys that shows {FREEWARE-VERSION-CAN’T-SHOW-THIS-KEY} for the Armadillo protector which cannot be seen nor deleted. We wanted to test the full version so badly that we donated to get it. From the “what’s new” area, we read that they’ve recently added a search routine for the latest Alawar.com games keys so we decided to put Alawar games to the test.
We downloaded a game from Alawar called Sticky Linky and played the whole free 60 minutes. Once the 60 minutes free play time is up, it shows 0 minutes game time left and we can no longer play the game until we purchase the game.
We ran Registry Trash Keys Finder full version and Alawar came up in the search results.
The Alawar key is deleted and running Sticky Linky now gives us another 60 minutes of free game time!
The Registry Trash Keys Finder full version has successfully extended the trial period of a game and it should also work for other software too. Other than just resetting the trial period, it also acts as a registry cleaner/optimizer where it detects obsolete registry keys of uninstall/app paths/SharedDLLs/Installer/MUICache/Help, unused file extensions, empty CLSID and TypeLib key, invalid name of CLSID and many more.
>>>>Download Registry Trash Keys Finder (Official : Freeware version)<<<<
>>>>Registry Trash Keys Finder Full Version (Unofficial)<<<<
[
UPDATED: The Link to the FULL version is currently
AVAILABLE.
]


























